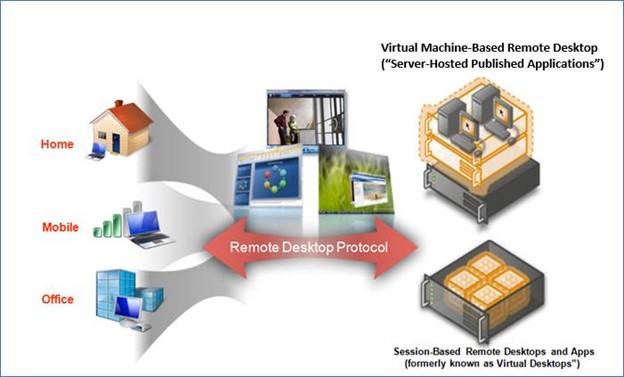
The Citrix account provides secure hosted virtual applications within a private cloud computing environment for State, County, Federal and local government entities of California, and empowers users with on-demand self-service to enterprise applications. Citrix is an application delivery solution that enables applications to be virtualized, centralized, and managed in the data center and instantly delivered as a service to users anywhere on any device.
Secure, anywhere, anytime, access to applications:
- Two-factor authentication
- Enterprise-class scalability
- Platform always up-to-date
- Core Microsoft Office Pro/Custom/COTS
Multiple costing models:
- Cost based on the number of user/concurrency
- Base application bundle
- Office Productivity bundle
- Custom/COTS application hosting
Fully managed solution:
- 24/7 Service Desk
- Self-service administration options
- Multi-layer anti-virus and email spam filtering
- Comprehensive data migration
Multiple access methods:
- Desktops/Laptops
- Tablets
- Mobile devices
Utilizing the Citrix account, client departments don’t have to worry about managing the virtual infrastructure, as this is handled by CDT. Infrastructure in this context can include the network, servers, user desktops, and hosted applications.
Further savings can be realized in organizations that accommodate BYOD (bring your own device), including laptops and tablets. Traditionally, most organizations have only grudgingly embraced BYOD due to security concerns. However, with Citrix, data is no longer stored on the users’ devices and is thereby not subject to viruses, theft, or other security issues. All data interaction is done on the remote, secure cloud infrastructure. The local device is only a window onto the remote experience.
Citrix accounts allow clients to streamline their infrastructure and reduce the expenditures associated with equipment and IT staff in exchange for a predictable “per user/per month” pricing model. It’s not that different from leasing a car instead of buying one.
- Included
- Optional Administration
- Hosting
- Custom Hosting
- Administration
- Roles & Responsibilities
- Storage
- Availability
- FAQs
- Rates
- Request
Citrix is an application virtualization solution that transforms desktops and applications into a secure on-demand service, available to any user, anywhere, on any device. With the Citrix account, you can deliver individual Windows, web, and SaaS applications, to PCs, Macs, tablets, smartphones, laptops, and thin clients with a high-definition user experience.
Base Application Bundle
Firewall Protection and Intrusion Detection
- All servers involved in the Citrix environment are positioned behind a firewall. Changes to the firewall rules must be approved by the CDT Information Security Officer (ISO).
- Connections to the Citrix environment are routed through a redundant Demilitarized Zone (DMZ) accessed via SSL only.
- Connections are double encrypted and compressed. A 128-bit SSL digital certificate provides the first layer of encryption. The second layer is provided via the Independent Computing Architecture (ICA) encryption and compression algorithm.
- Access security is enhanced by the use of a secure token code along with the standard user ID and strong passwords
Secure Tokens
CDT provides industry-standard security using hardware and software protocols and (OTP) to protect the Citrix environment from unauthorized access. Tokens can be hardware (hard token), software (per device), or Smart Phone (app).
Requirements
Refer to the Supported Client OS and Browsers list for more information regarding supported client operating systems and browsers.
High Availability
Featuring Microsoft clustering technology, CDT has architected the Citrix environment to maximize operational availability through redundancy and failover to reserve servers.
Security
In addition to the same security provided for our Application Hosting service, the Citrix environment features network security, physical security, criminal background checks on administrators, and encryption in transit and at rest. The Citrix environment holds the following security certificates:
- Health Insurance Portability and Accountability Act (HIPPA) compliant
- Sarbanes Oxley (SOX) compliant
- Payment Card Industry (PCI) compliant
- Customers are expected to observe the various IT security-related best practices, standards, and policies in force within OTech including:
- SIMM 66A and 70E State of California Telework and Remote Access Security Standard
- IT Policy Letter ITPL 10-03, SAM Manual section 5340 and the International Standards Organization section 17999
For more information, see Security Services.
Microsoft
Current versions hosted in the environment includes Microsoft Office 2013, Microsoft Office 2010, Microsoft Office 2007, and Microsoft Office 2003 (legacy apps).
Microsoft Office Productivity Bundle
The Microsoft Office Productivity Bundle consists of Microsoft Office Pro:
|
|
|
|
|
|
Standalone Microsoft Products
- Microsoft Visio – (Standard)
- Microsoft Project – (Standard)
Adobe
- Adobe Acrobat Professional
Hosted Customer COTS Application(s)
The Citrix environment offers a flexible mix of cloud, dedicated, and hybrid hosting services to meet the needs of your application(s). Applications are diverse and they come with their own requirements and technical nuances. The Server Based Computing support group has the experience and expertise to help you, by certifying your application in our environment and designing an infrastructure that’s best suited for your application.
The Citrix environment offers a flexible mix of cloud, dedicated, and hybrid hosting services to meet the needs of your custom application(s). Applications are as diverse and unique as the business units that develop them, and they come with their own requirements and technical nuances-from varying compute, storage, and security needs, too often unpredictable load. The Server Based Computing support group has the experience and expertise to help you, by certifying your application in our environment and designing an infrastructure that’s best suited for your custom application. If dedicated servers are required to meet the custom hosting application need, additional charges may apply.
Server Based Computing supports distributed administration and self-service password resets.
Backup and Restore
Operating System Backup
- Weekly backup of the operating system.
Data Backup
- Full backups occur every Saturday
- Incremental Backups occur three times a day.
Consulting
CDT bills for consulting services when requested services exceed the workload in the rates approved. For more information please see Consulting Services.
Optional Administration
Consulting
CDT bills for consulting services when requested services exceed the workload in the rates approved. For more information see Consulting Services.
Migration Planning
The Citrix environment Migration Planning Services are a one-time fee based on the number of hours spent on your project.
- Site Discovery
- Detailed discovery document
- Readiness Assessment
- Migration Planning
- Access
- Applications
- Customer service validation/acceptance support
- Data
Training
CDT offers on-site and/or Web conferencing-based training available for all users.
Role CDT Customer
Application deployment - Assign applications to AD user groups per Customer Request. X
Applications - Ensure appropriate O365 or Custom Application licensing and management. X
Applications - Provide a deployable application package (MSI or EXE). X
Applications - Provide a list of applications to be used by the Customer's organization. X
Applications - Provide applications updates – packaging, coordinating deployment with the CDT team. X
Change management - Maintain a Change Management process and provide a single-point-of-contact to the CDT service team. X
Change management - Notify Customers, in advance when changes will be made to their Citrix environment. X
End-user support - Line-of-business applications: custom software, 3rd-party software, design tools, and anything not specified in this document. X
End-user support - Onsite infrastructure - all network and internet connectivity, client device configuration, peripheral devices, proxy server, firewalls, and WAN connectivity. X
End-user support - Provide end-user support for the Citrix Services running on CDT systems.
Note: This does not include the support of End-User’s end-point device, LAN or WAN connectionsX
Identity management - Create user accounts, assigning users to groups and keeping metadata up to date. X
Identity management - Request Citrix user accounts. X
Identity management - Specify users to groups. X
Infrastructure service support - Deploy approved applications to client’s CDT Citrix environment. All applications will go through a certification process. X
LAN network infrastructure - Setup, configuration and management (including troubleshooting and debugging) of all networking-related infrastructure and services, including internet connectivity, network controls, proxy configuration and remote connectivity infrastructure.
By default the CDT Citrix does not specify or require a proxy server; however, if one is configured (in hardware or software), there is a collection of URLs that must be allowed by the proxy server. The customer is responsible for troubleshooting any conflicts or incompatibilities due to proxy serversX
LAN network infrastructure - Troubleshooting any conflicts or incompatibilities due to proxy servers. X
Mobile devices - Mobile device management hardware, accessories and software, security and connectivity. X
Printing - Install, maintain and administer local printers and local print queues. X
Security monitoring - If a threat is detected by the CDT team or CDT Security Operations Center (SOC), notify the customer, isolate the Citrix Account, and rectify the issue. X
Security monitoring - Monitor customer Citrix environment. X
Security monitoring and response - If a security incident is detected which is outside the scope of CDT Server Based Computing, provide a list of preferred customer contacts based on the severity of the issue. X
Security monitoring and response - Investigate and resolve incidents for non-CDT Server Based Computing and ensuring that the CDT Server Based Computing Team is informed of any issues that may impact the service (Local Virus or DDOS attack). X
Update monitoring and management - Actively monitor custom Citrix environments to ensure that the latest quality, features, and definition updates are installed according to CDT security policies. X
- SAN storage is available in increments of 1 MB.
- Data storage on disk using a redundant array of independent disks (RAID)
- Off-site storage
Maintenance Schedule
What is Citrix?
The Citrix Service provides secure hosted virtual applications within a private cloud computing environment for customers and empowers users with on-demand self-service to enterprise applications.
Citrix is an application delivery solution that enables applications to be virtualized, centralized, and managed in the CDT data center and instantly delivered as a service to users anywhere on any device.
How secure are Citrix Services?
CDT provides industry-standard security using hardware and software protocols and one-time passwords to protect the Citrix environment from unauthorized access.
Important security features include:
- Two-factor authentication
- Firewall Protection and Intrusion Detection
What is the cost of Citrix Services?
Depending on the services selected, the monthly rate can range between $17.40 – $52.20 per user.
Costs are based on:
- Base application bundles
- Office Productivity bundles
- Custom or COTS application hosting
Is Citrix a fully managed solution?
Yes, CDT fully manages and the service includes:
- 24/7 Service Desk
- Self-service administration options
- Multi-layer anti-virus and email spam filtering
- Comprehensive data migration
How do I purchase Citrix?
To Add, Change, or Delete a Citrix Account, submit a Case/Request at https://services.cdt.ca.gov/csm
The rate schedule represents standard CDT services. If a Customer requires technology solutions that are not part of the standard, CDT will review the Customer’s request and provide customized pricing as necessary.
Subscriptions to this service are available.
Service Description Service Identifier Product Name Unit of Measurement Rate Service Code Notes
Base Application Bundle Below 50% Concurrency Citrix Monthly/Per User $17.40 M701
Base Application Bundle 50% - 74% Concurrency Citrix Monthly/Per User $25.20 M702
Base Application Bundle 75% - 100% Concurrency Citrix Monthly/Per User $31.80 M703
Office Productivity Bundle Below 50% Concurrency Citrix Monthly/Per User $37.80 M704
Office Productivity Bundle 50% - 74% Concurrency Citrix Monthly/Per User $45.60 M705
Office Productivity Bundle 75% - 100% Concurrency Citrix Monthly/Per User $52.20 M706
Microsoft Visio Standard Win32 w/Software Assurance Citrix Monthly/Per License $6.50 M708
Microsoft Project Standard Win32 w/Software Assurance Citrix Monthly/Per License $19.50 M710
Adobe Acrobat Pro Citrix Monthly/Per License $6.50 M712
Citrix Storage Citrix Monthly/Per MB $0.0044 M714
Secure ID Physical Token (Monthly Payment Option) Citrix Monthly/Per Token $3.30 M715
Secure ID Software-based Token (Monthly Payment Option) Citrix Monthly/Per Token $1.80 M716
Service Request Name Link
Citrix Account
Add, change or delete Citrix Account services using the Server Based Computing Service catalog item.Order SBCS Services